Cyber security provider Check Point has shed light on the new wave of cyberattacks that have hit Iranian state infrastructure in the past few months.
The American-Israeli software and hardware security company said in a comprehensive technical analysis published on February18 that the recent wave of attacks that caused major disruptions to public services are far from minor website defacements.
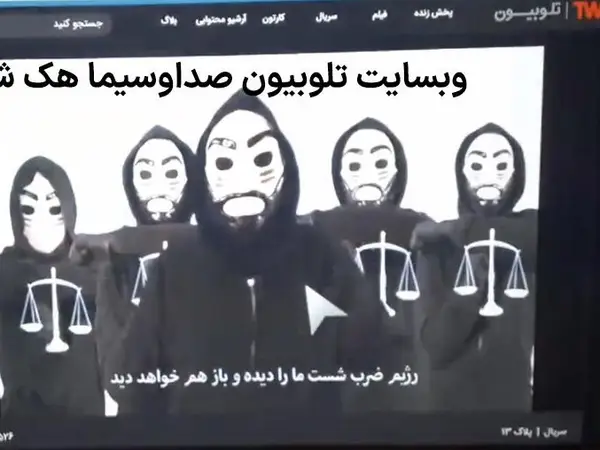
The report provided in-depth breakdowns for some of the attacks, including the targeted hack of the state broadcaster (IRIB) in late January, saying the attackers’ aim was also to disrupt the IRIB’s programs, with the damage to the TV and radio networks possibly more serious than officially reported.
Several television and radio channels of the state broadcaster were hacked on January 27 with photos of leaders of an opposition group briefly aired. The image of Massoud and Maryam Rajavi, leaders of the Albania-based opposition Mujahideen-e Khalq (MEK), were broadcast for around 10 seconds with audio footage from one of their speeches in the background.
After the picture of the MEK leaders, the video showed a photo of Iran’s Supreme leader Ali Khamenei with a red cross on it, as an off-camera voice said, “Death to Khamenei.” Khamenei was badly injured in 1981 in one of a series of bombings attributed to the MEK.
Check Point research team probed the cyberattack and was able to retrieve the files and forensic evidence from publicly available resources, finding malicious executables whose purpose was to air the protest message, as well as evidence that a wiper malware was used.
The security firm provided a technical analysis of the tools used in the attack, as well as the attackers’ tactics, identifying malware that takes screenshots of the victims’ screens, several custom-made backdoors, and related batch scripts and configuration files used to install and configure the malicious executables.
Check Point also gave a detailed report about other major cyber-attacks such as an attack that hit the Iranian national railway and cargo services in July 2021. The attack caused “unprecedented disruptions” to the country’s trains, a day before media outlets reported that the website of Iran’s Roads Ministry, in charge of transportation, was taken down in a ‘cyber disruption’, preventing access to their official portal and sub-services.
A message was also displayed on the train schedule boards referred perplexed passengers to the Supreme Leader’s office phone number.
A group called ‘Predatory Sparrow’ claimed responsibility for the attacks, whose tools and tactics were used in similar operations against private companies in Syria by an anti-regime group called Indra.
In August 2021, the hacktivist group Tapandegan (Palpitations), previously known for hacking and displaying protest messages on the electronic flight arrival and departure boards in Mashhad and Tabriz international airports in 2018, released security camera footage from Tehran's Evin Prison, where many political prisoners are held. Tapandegan said the images had been acquired by hackers called Edalat-e Ali (Ali's Justice) and were being circulated to draw attention to human rights violations, particularly against political prisoners.
In October 2021, all gas stations in Iran were paralyzed by an attack that disrupted the electronic payment process, leading to extremely long queues for two days that prevented customers from paying with the government-issued electronic cards used to purchase subsidized fuel. When the card was swiped for payment, the supreme leader’s office phone number appeared on the screen. Iranian officials claimed that foreign actors, such as Israel and the US, were behind the attack. However, Predatory Sparrow claimed responsibility for this attack as well.
On February 1, the web-based streaming platform of IRIB, Telewebion, was hijacked yet again to broadcast protest messages urging citizens to rebel and stating that “the regime’s foundations are rattling” in the middle of a live broadcast of the Iran-UAE soccer match.
Recently, on February 7, 2022, the Edalat-e Ali group released footage from closed-circuit cameras in another Iranian prison, Ghezel Hesar.
Check Point says it is still not clear how the attackers gained initial access to these networks that are “completely isolated, are equipped with acceptable security protocols and are not accessible via the Internet”.
It concluded that “the actor may have many capabilities that have yet to be explored. On the one hand, the attackers managed to pull off a complicated operation to bypass security systems and network segmentation, penetrate the broadcaster’s networks, produce and run the malicious tools that heavily rely on internal knowledge of the broadcasting software used by victims, all while staying under the radar during the reconnaissance and initial intrusion stages”.
Check Point also concluded that “the attackers’ tools are of relatively low quality and sophistication and are launched by clumsy and sometimes buggy 3-line batch scripts”, which supports their “theory that the attackers might have had help from insiders or indicate a yet unknown collaboration between different groups with different skills”.